Passwordless Authentication for Domain-Joined Machines

Passwordless Authentication Introduction
The Secret Double Octopus passwordless authentication platform is a highly scalable, reliable and easy to use system designed to help organizations large and small increase their security and improve their end user experience. Direct Business Technologies is a strategic partner and integrator of the Secret Double Octopus platform. You can find additional details about our passwordless authentication services here.
The Secret Double Octopus platform eliminates the need for users to enter in passwords across the enterprise. Secret Double Octopus provides many integration capabilities for organizations to integrate applications and authentication flows into the passwordless authentication process.
Common integrations for passwordless authentication:
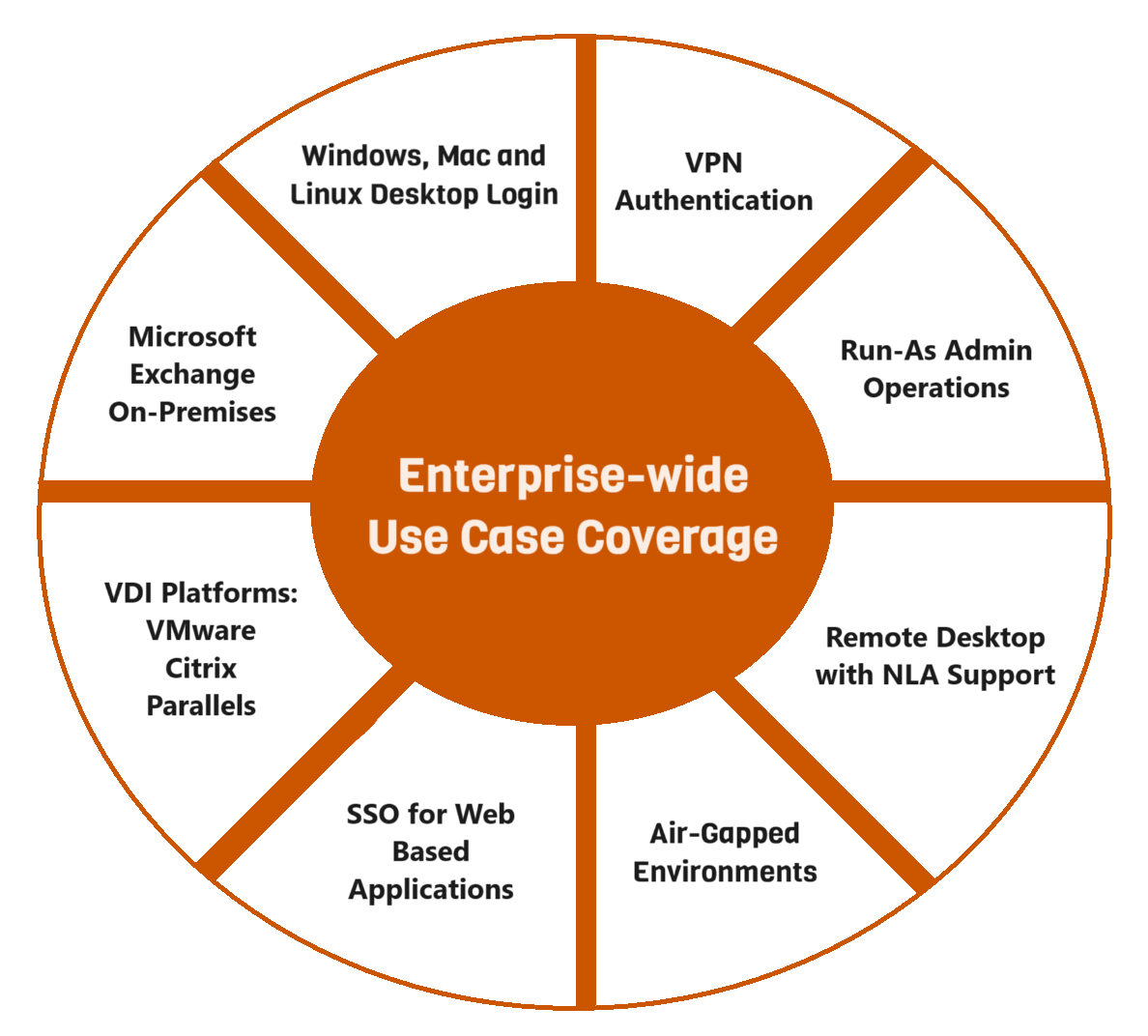
- • Windows, Mac and Linux Desktop Login
- • VPN Authentication
- • Run-as Admin Operations such as PowerShell
- • Remote Desktop with NLA support
- • SSH Authentication
- • Web based Single Sign On (SSO) based applications via the SAML 2.0 Protocol (Microsoft 365, Okta, Google Workspace, CRM platforms, Helpdesk systems, etc)
- • VDI Platforms such as Citrix, VMware, and Parallels
- • Microsoft Exchange On-Premises
- • Custom/Legacy application integration
- • Air-Gapped environments such as SCADA networks
Benefits of going passwordless:
- • Increased security by eliminating password reuse
- • Increased security by enforcing multi-factor authentication on every authentication
- • Increased security by implementing phishing resistant MFA
- • Regulatory compliance for various standards including PCI-DSS, HIPAA, SOX, SOC2, CMMC, DFARS, FedRAMP, FTC Safeguards
- • Reduced helpdesk call volume – on average, customers reduce their helpdesk support calls by 30% due password reset and account lockout tickets virtually disappearing
- • Improved employee morale – removing barriers to performing employees jobs improves employee satisfaction and leads to employees retention rate increases
- • Improved employee productivity – Employee productivity increases are common after passwordless authentication implementation due to less time spent on support calls getting passwords reset and accounts unlocked
Let’s dive into what passwordless authentication from Secret Double Octopus provides for organizations big and small. This blog post is focusing on providing an overview of the end user experience for Windows Active Directory domain-joined machines.
We will be reviewing the Secret Double Octopus authentication platform with server version 5.8.2 in this blog post.
The End User Experience
Seeing is believing! Below are two videos and details of these configurations showing typical authentication scenarios within the Microsoft Windows operating system.
Domain-Joined Workstation Login Experience
This video provides a quick demo of the end user experience to log into a domain-joined Windows machine using passwordless authentication from Secret Double Octopus. Below the video we go into details on what is happening under the hood. The steps to login are easy:
- 1. Enter your username
- 2. Select your authenticator (if applicable)
- 3. Approve push notification
- 4. Supply your biometric, faceID, or phone passcode to your mobile device
- 5. Get signed in (note, the video below showcases an adaptive MFA process for first time login which adds an extra step)
Run-As/CredUI Prompts
This video shows the authentication experience for run-as operations and remote desktop NLA prompts. The Secret Double Octopus credential provider invokes anytime the operating system invokes an authentication prompt. In this example, I am logged into my demo machine as user ‘DBTLAB02\justin’ and will be running powershell as admin. This will showcase SDO protecting CredUI prompts and that SDO can support multiple accounts on the same mobile authenticator app.
- 1. Select Run as (Powershell as Admin in this example)
- 2. Select authenticator, if required
- 3. Approve request on mobile authenticator
- 4. Supply biometric/faceID/phone passcode
Authentication Flow
Wondering what exactly just took place in the above videos? Here is what is happening at a high-level in the authentication flow.
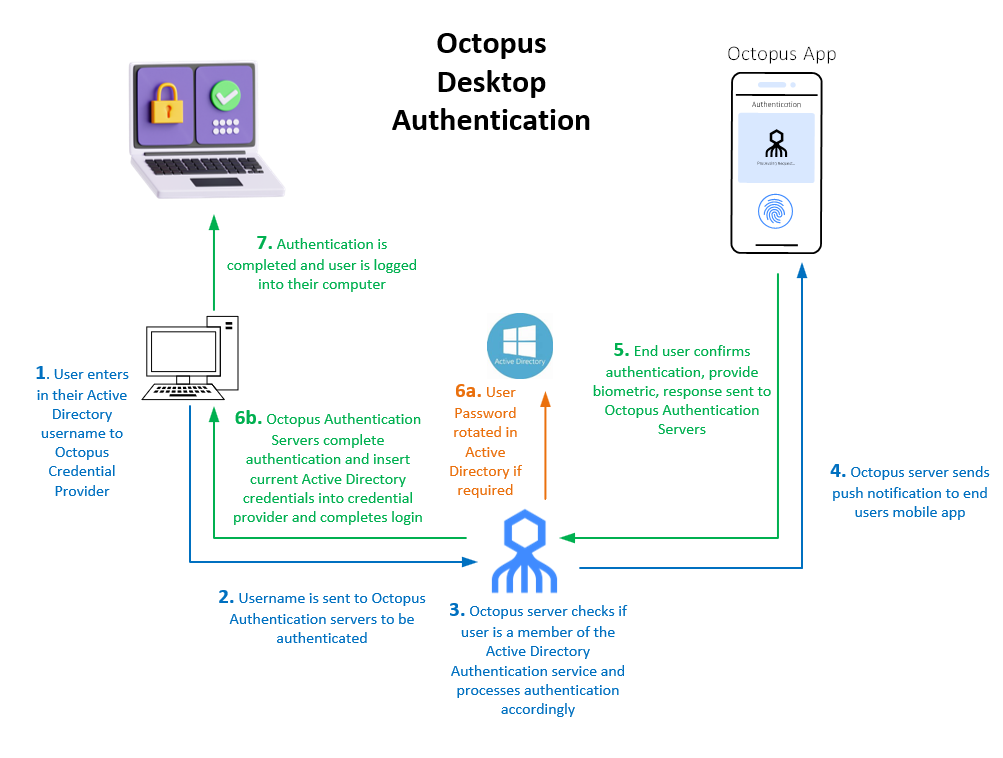
- 1. User enters in their Active Director username to the Octopus Credential Provider
- 2. Username is sent to Octopus Authentication servers to be authenticated
- 3. Octopus server checks if the user is a member of the Active Directory Authentication service and processes authentication accordingly
- 4. Octopus server sends push notification to end users registered mobile device/Octopus Authenticator app
- 5. End user approves the authentication on their trusted device (First Factor) and supplies their Fingerprint/FaceID/Passcode to confirm their identity (Second Factor)
- 6. If required, SDO will change the user’s password in Active Directory, otherwise it sends the stored credential from its password vault down to the workstation
- 7. The password is decrypted using the machine certificate private key and inserted into the Windows Credential Provider in the background and the user is logged into their machine
What the Heck? It’s Changing My Password?!?
You got it! From a workstation logon perspective, Secret Double Octopus acts as a very sophisticated password manager and vault (this is the easiest way to describe it). To provide the greatest level of flexibility and integration with on-premises and legacy based applications, SDO is maintaining the use of passwords on user objects within Active Directory. When users log into their domain-joined machine through SDO for the first time, the platform will take control of the users credential and set a new password in Active Directory. Once the password is changed in Active Directory, this password is then sent down to the users machine and inserted into the custom Windows credential provider in the background, completely seamless to the end user.
Before user credentials are changed, the following conditions must be met:
- 1. The user’s machine has connectivity to an Active Directory domain controller (Otherwise how would the machine validate the new credential?)
- 2. The user’s current credential in Active Directory is older than the age of the password policy setting in the directory settings of the Secret Double Octopus directory configuration
OR
The user’s account has been flagged to force password rotation at the next logon by an administrator - 3. The authentication being performed is going through the Active Directory Authentication service in Secret Double Octopus (Basically, a logon to the computer, not a SAML or RADIUS server)
- 3b. There is an option to allow an LDAP based application authentication to rotate passwords, there are specific scenarios to use this, but that is out of scope for this blog post
Password Policy
Password rotation for end users is controlled by a password policy that is unique per directory within the Secret Double Octopus platform. The password policies within Secret Double Octopus determine how often a password is rotated, how long to set the password and what type of characters to use. This password policy must meet the minimum requirements within Active Directory. If your AD policy requires 14-character passwords, you must set the password policy within the SDO directory to be a minimum of 14-characters, or the password rotation will fail.
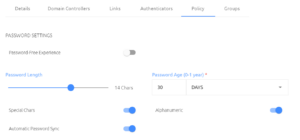
| Setting | Description |
|---|---|
| Password-Free Experience | This setting, in conjunction with a setting on the Octopus Desk credential provider, tells the SDO platform not to change the users password. End users are prompted to enter their password on the first authentication, then once they complete the Octopus authentication, their credential is vaulted into the SDO password vault and the user is not prompted for their password again |
| Password Length | This setting determines how long of a password SDO will set on the user object. This setting must at least match your Active Directory password policy for minimum length |
| Password Age (0-1 year) | This setting determines the age at which SDO should rotate the users password. When a user authenticates to their machine and their password is older than this setting, their password will be rotated as long as their machine has connectivity to Active Directory |
| Special Characters | This setting tells SDO to use special characters such as (!@#$%^&*) in the password |
| Alphanumeric | This setting tells SDO to use alphanumeric characters in the password |
| Automatic Password Sync | When this setting is on, SDO will rotate the users password if it is out of sync with the SDO password vault. Typically this happens if the users credential was reset by an administrator directly in Active Directory |
Authenticator Options
The Secret Double Octopus platform offers a wide range of authenticator options to provide the most flexibility possible for your organization. There is no additional license required from Secret Double Octopus to utilize these authenticator options.
| Authenticator Name | Authenticator Description | Authenticator Features | Phishing Resistant? |
|---|---|---|---|
| Octopus Authenticator App | A powerful mobile authenticator app designed for the best experience with the Secret Double Octopus platform | Support for Android and iOS, encrypted and highly secure with BLE high-assurance support for workstation login. Offline authentication support via BLE. Ability to view current Active Directory credential on the mobile app. |
Yes |
| FIDO2 Keys | FIDO2 keys for phishing resistant passwordless authentication | Wide range of FIDO2 authenticators provides flexibility for customers. Utilize NFC for Tap authentication or insert your key into the system. Ensures physical presence at the machine being logged into. Biometric and PIN based authentications supported. | Yes |
| Passkeys | Passkeys utilizing end user devices with no application to install – *Not yet supported for workstation login, only supported for SAML authentication | Allow your end users to utilize their existing mobile device, using phishing resistant MFA without the need to install an authenticator app. Passkeys can be used to retrieve credentials from the Octopus Desk systray to suppor custom onprem workflows for legacy applications. | Yes |
| Certificate Authenticator | Utilize certificates as an authenticator, integrate in with existing PKI and Smartcard devices. | This authenticator allows you to utilize existing smartcard devices, including HID badges that support smartcard/certificates. This allows you to keep existing investments and utilize them. This does not change user objects in Active Directory to be smartcard or certificate logon users. This option is using the certificate + PIN to perform the MFA, SDO confirms the certificate against your internal certificate authority. | No |
| OTP | Utilize OTP codes for passwordless login. Support for both hardware tokens and soft tokens | Supports hardware tokens. Supports software OTP clients such as Google and Microsoft Authenticator apps. | No |
| 3rd Party – Forgerock | Forgerock authenticator app for customers with the Forgerock platform | Allows organizations to utilize their existing Forgerock deployment and trees to authenticate users via the Forgerock app. Customers that have deployed a custom app using Forgerock SDKs can utilize their custom app through this method. | No |
| 3rd Party – Okta Verify | Allows organizations that utilize Okta as their IDP to use Okta Verify as their mobile authenticator | Requires Okta to force the MFA push on all authentications, easy integration through API and authentication policy within Okta | No |
| 3rd Party – Duo | Allows customers with existing Duo deployments to utilize the Duo authenticator app as their mobile authenticator | Utilizes Duo push notifications and policies | No |
| 3rd Party – RSA | Allows customers with existing RSA mobile authenticators to utilize the RSA app as their mobile authenticator | Integrates with existing RSA deployments, utilizes push notifications and RSA policies | No |
That’s a Wrap!
Thanks for reading! We hope that you found this post showcasing passwordless authentication for domain-joined machines helpful. If you would like to get a personalized, in depth demo of the platform, feel free to reach out to us via our contact page. If you are an existing Secret Double Octopus customer and would like to discuss our services, please let us know!
Feel free to browse additional blog post content here.