Secret Double Octopus Server 6.6 Release Notes and Highlights

Welcome!
Welcome to our blog! Today, we’re excited to discuss the recent release of Secret Double Octopus (SDO) Server version 6.6, launched on January 13, 2025. We are excited for this release and are still working through some of the new features in our lab environment. This release is significant for many reasons, but a big reason is that it makes a big step forward in unifying the code base between the SDO On-Premises version and their SaaS hosted version. Merging the code bases will allow for a more streamlined development process, resulting in faster development cycles and new features coming to market faster.
What’s New in Secret Double Octopus 6.6
Octopus Authentication Server version 6.6 introduces a variety of features that simplify and streamline the user authentication experience while maintaining the highest levels of security. Many of these new features require the latest version of the Octopus Desk agent (The Windows credential provider) to be deployed. It is strongly recommended to use Octopus Desk for Windows v4.0.1 / Octopus Desk for Mac v3.0.2 and to encourage users to download the latest version of the Octopus Authenticator mobile app.
Desktop SSO
We are excited about this feature. This is one of the features we still need to get up and running in our lab environment, but it is really great for organizations that still have legacy applications that do not fully support federating authentication to a third-party provider. Examples of this would be applications that rely on credentials stored in a Microsoft SQL Server database or an application that can only authenticate via an LDAP BIND to domain controllers or applications that are performing Windows Integrated Authentication and passing the credentials through the host server OS.
An example of this use case would be a banking platform that does not or is not tied into Active Directory or a third-party IDP and relies on internal application users for authentication. Secret Double Octopus can integrate with the application and start to perform passwordless authentication for users by taking control of their user credentials within the application itself. This increases security by ensuring ephemeral tokens are used for the credential, as well as making it easier for end users by providing them with easy-to-use passwordless authentication.
This feature requires the Octopus Desk client version 4.0.1 or higher to work. If you are integrating with a SQL based application, an additional SQL agent is required for SDO to integrate with the database. Finally, there is a process required to map out the legacy application windows and their username and password fields. Once this is completed, SDO will be able to replace user credentials with the secure tokens and know the application window names and fields to inject the credentials where required.
Here is what SDO’s release notes say about this:
Octopus Authentication Server now supports application integration, enabling Windows users to seamlessly access these applications without manually entering login credentials. When an integrated application launches, the Windows Agent retrieves user credentials and automatically populates the fields of the Login screen. This automatic population occurs through definition of Desktop SSO elements for the integrated application in the Octopus Management Console. When defining application settings, the system admin specifies properties and parameters of the Login window and its fields. These attributes are automatically saved to a configuration file which is then deployed to workstations, allowing the Windows Agent to identify the Login window and set user credentials in the appropriate fields.
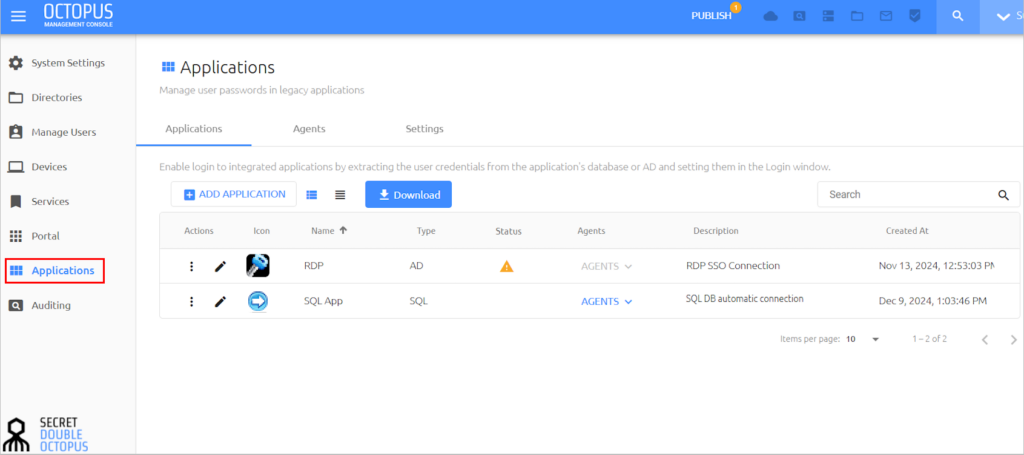
If you have a pesky legacy application that requires your Active Directory credential or only supports users created within the application, this release may provide your organization with a way perform secure, passwordless multi-factor authentication on these systems. Feel free to CONTACT US if you have an application you would like to discuss taking passwordless with Secret Double Octopus.
WS-Federation Support
This release brings a dedicated WS-FED service within the Secret Double Octopus platform. SDO has WS-FED support in server version 6.4.2, however it is tied into their SAML service. In version 6.6, they have separated this out into its own service within the platform. Separating WS-FED out to its own service provides clarity in the platform as well as makes it easier to integrate future applications. This also sets the stage for new features to be added easily to the WS-FED service and reduces the overall amount of development time due to reduced QA testing.
SDO release notes state:
The new dedicated WS-Fed service provides integration between the Octopus Authenticator and the WS-Federation mechanism. The service enables full-scale integration with Entra ID, allowing use of the Octopus platform on Entra ID domain-joined machines. It also supports integration with mobile device management systems, e.g., Microsoft Intune.
Entra ID External Authentication Support
Back in 2024, Microsoft released a notice that they would be enforcing a new method to confirm that MFA was performed on an authentication using a federated or third-party identity provider. Details on that can be found at this Microsoft article. The short version of this is that Microsoft was moving away from accepting a claim via SAML 2.0 and is requiring Open ID Connect (OIDC) to satisfy the claim that MFA was performed. Until this release, SDO did not have OIDC support. The newly released Entra ID service in SDO provides the required integration point to support this Microsoft requirement.
SDO release notes state:
The new Entra ID EAM service enables users to log into the Microsoft Entra admin center using the Octopus platform as a means of two-factor authentication.
Check back soon for another blog post outlining how to integrate Secret Double Octopus into the Microsoft External Authentication platform.
Adaptive Authentication for RADIUS Services
This feature is not a common of a need, but for customers running applications that authenticate via RADIUS AND support two-factor authentication, SDO can now support a second factor when using push notifications. This feature is not applicable to users of FIDO2 tokens or users that are in Bypass mode.
SDO release notes state:
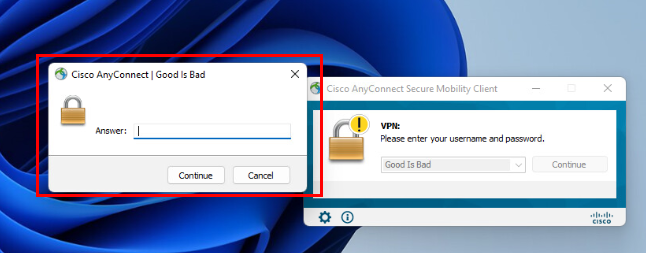
Octopus Authentication Server now supports the option for strong authentication for login to RADIUS services, such as VPN solutions that support two-factor authentication. When this feature is enabled, users need to enter the verification code that is generated and displayed in the Octopus Authenticator mobile app after the push authentication request has been approved. The following figure shows an example of a dialog prompting users to enter the code:
Biometrics Data Monitoring Enhancements
This new feature is subtle, but powerful. With this feature, organizations can now automatically lock an authenticator if the authenticator app detects that the biometric on the device has changed. This helps bolster security and ensure that users are not fraudulently adding people to their devices, being forced to provide their mobile authenticator to someone else etc.
SDO release notes state:
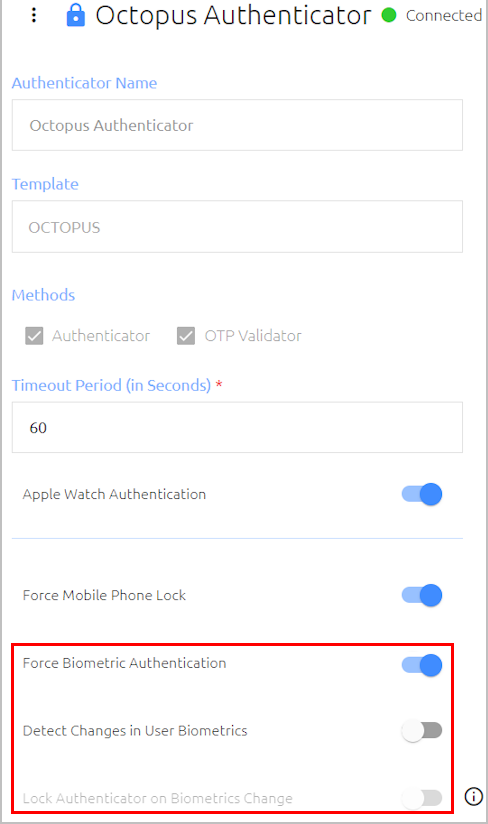
Octopus Authenticator settings (in the Octopus Management Console) now allow the system admin to choose whether to disable the authenticator upon changes in biometrics data. When the Detect Changes in User Biometrics toggle is enabled, the mobile app checks for changes in biometrics with every authentication request, and detected changes are recorded as an auditing event. When the new Lock Authenticator on Biometrics Change toggle is also enabled, the app blocks authentication and the mobile authenticator is disabled. The user cannot work with the account until it is re-enabled by the admin in the Octopus Management Console.
Note: To use these features, the Force Biometric Authentication toggle must be enabled.
Audit Enhancements
This is a minor enhancement adding the session ID to the audit logs for enrollment requests. This is useful if you are troubleshooting an enrollment failure.
SDO release notes state:
Session ID is now included in auditing records for enrollment requests.
Publish Enhancements
This is another minor set of enhancements to optimize the publish time (committing changes to all auth servers). Smaller organizations will likely not notice much change from this. Larger organizations with 10’s of thousands of users will notice a performance boost when publishing.
SDO release notes state:
Octopus Authentication Server version 6.6 introduces several new configurations for optimizing publish time.
Looking to integrate passwordless authentication into your organization?
Whether you’re modernizing legacy applications or enhancing security across your systems, the latest features in Secret Double Octopus Server 6.6 offer exciting possibilities. Let’s discuss how passwordless MFA can transform your organization’s authentication strategy.
📩 Contact us today to explore tailored solutions and start your journey to a passwordless future! CONTACT US to learn more about Secret Double Octopus and our services.
Check back again soon for new blog posts on Secret Double Octopus and other technology topics. Our next blog post will be on integrating SDO with the newly released Microsoft External Authentication Methods, as described earlier in this post.