Secret Double Octopus Server 6.6.2 Release Notes and Highlights

Welcome!
Welcome to our blog! Today, we’re excited to discuss the recent release of Secret Double Octopus (SDO) Server version 6.6.2, launched on February 13, 2025. This release builds upon version 6.6 that was released on January 13th, 2025. We are excited for this release and are still working through some of the new features in our lab environment. The highlight of this release is support for native Entra ID (Azure AD) joined devices without on-premises AD. This Graph API integration enables full passwordless MFA for Entra ID joined devices.
What’s New in Secret Double Octopus 6.6.2
Octopus Authentication Server version 6.6.2 introduces a variety of features that simplify and streamline the user authentication experience while maintaining the highest levels of security. As some of these features require the latest Agent versions, it is strongly recommended to use Octopus Desk for Windows v4.0.2 / Octopus Desk for Mac v3.0.3 and to encourage users to download the latest version of the Octopus Authenticator mobile app.
Entra ID directory type enhancements
This feature opens new opportunities for organizations transitioning to native Entra ID and eliminating on-prem AD. SDO is, to our knowledge, the only third-party solution offering passwordless MFA for native Entra ID joined devices without on-prem AD. While Microsoft does have Windows Hello for Business that they push heavily for passwordless authentication, Secret Double Octopus provides advantages over the WHfB option.
SDO release notes state:
Octopus Authentication Server now supports two options for integrating users in Entra ID directories. The Entra ID directory type, which uses the Microsoft Graph API, does not require LDAP or a PI Entra ID license. The Entra ID (LDAP) directory type uses the LDAP protocol, which requires a PI Entra ID license.
IMPORTANT: Migration from an Azure AD directory type to either Entra ID directory type is not supported. It is also not possible to migrate from one type of Entra ID directory to the other.
For more details about adding and configuring directories, please refer to the Octopus Management Console Admin Guide.
Support for account recovery
This quality-of-life feature simplifies account recovery for users and administrators. Administrators can enable self-service account recovery, reducing helpdesk tickets. This is a system-wide toggle, either enabled or disabled. To manage this setting, go to System Settings > Authenticators Tab > Edit Octopus Authenticator > Mobile Device Recovery toggle.

SDO release notes state:
The new Mobile Device Recovery toggle in the Octopus Authenticator settings (in the Management Console) allows the system admin to choose whether or not to support account recovery after migration to a new mobile device. Note: Previous configuration of this feature in the prod.json file will NOT be saved upon upgrade. The setting needs to be configured in the Management Console after upgrade.
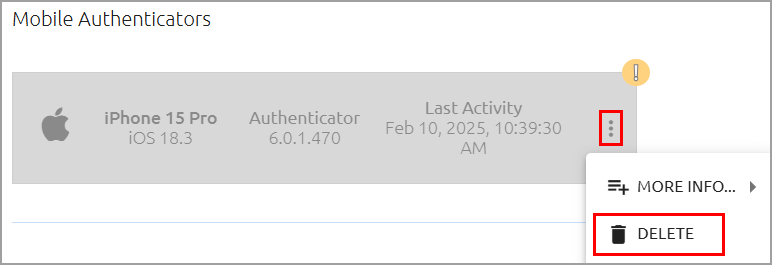
Deleted mobile account handling enhancements
This enhancement improves usability and security. If a user deletes an account from their Octopus Authenticator app, that will now be reported back into the management console and the authenticator will automatically be disabled (not deleted). Admins and helpdesk staff receive a visual cue when a user deletes their account. This streamlines support and helps identify mistakenly removed authenticators.
SDO release notes state:
If a user has deleted an account on the mobile device, the Mobile authenticator in the Management Console (under user details) becomes disabled, with an alert icon displayed in the upper right corner. The authenticator can no longer be used, receive push messages, or be enabled. The Delete action is available to remove the authenticator from the system.
Octopus Management Console UI enhancements
This release improves the management console UI with the following enhancements:
Detailed description of FIDO devices
This enhancement provides additional details of the individual FIDO authenticators registered to a user account. Specifically, it is showing the make and model of FIDO key.

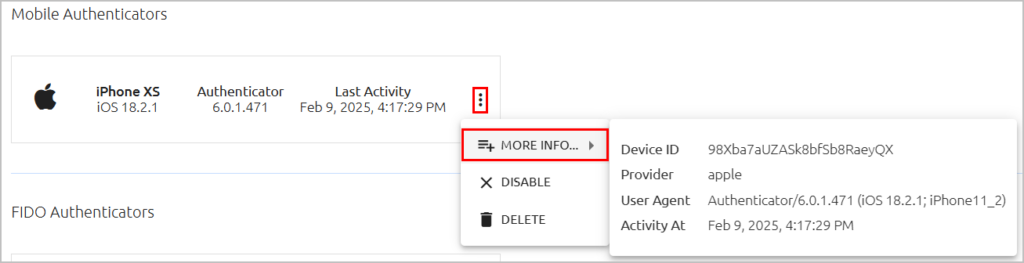
Mobile authenticator details
Mobile authenticators now display additional details, including the Device ID.
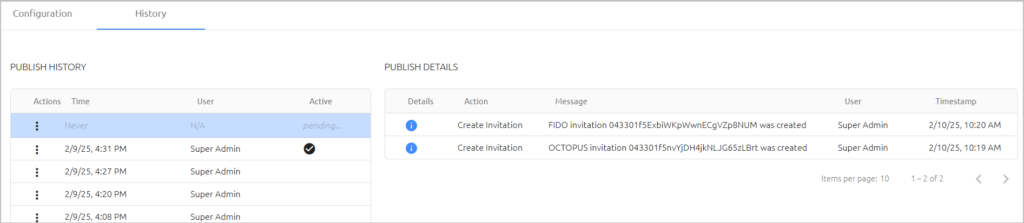
List of unpublished changes
By default, the Publish Details pane of the History sub- tab (System Settings > Publish) now displays a list of all currently unpublished changes (pending for the next publish operation).
Management Console Login with Octopus Authenticator Toggle
The Secret Double Octopus management console login screen now retains the last selected state of the Login with Octopus Authenticator toggle (enabled or disabled), and automatically presents that state for the next login.
Target URL for integrated applications
This Secret Double Octopus feature is an expansion of the integrated applications feature released on January 13th in version 6.6 of the Octopus platform. This enhances security by ensuring credentials are only injected into authorized application URLs.
SDO release notes state:
Settings for integrated applications now include an optional Application URL field for enhancing the security of Desktop SSO authentication to web applications. When the setting is present, the Windows Agent checks the target website to avoid accessing incorrect or malicious sites.
Expansion of Helpdesk role permissions
In response to customer feedback, SDO has expanded the Helpdesk role to allow additional operations. The helpdesk role can now, by default, perform a directory synchronization and unblock a workstation within the management console.
SDO release notes state:
Users with a role of Helpdesk are now authorized to perform directory synchronization and unblock workstations for users.
Audit enhancements
This is a minor update adding additional clarification and fixes to audit log entries.
SDO release notes state:
Octopus Authentication Server version 6.6.2 includes several clarifications and fixes related to audit messages.
Bug Fixes
SDO has fixed a bug in the bypass email notifications. Previously, email notifications did not include the bypass duration. While the affected versions aren’t specified, we believe this impacted version 6.6.
SDO release notes state:
Octopus Authentication Server version 6.6.2 contains the following bug fix:
| Issue Number | Issue Description | Current Status |
|---|---|---|
| SSA-15750 | Length of bypass period missing from email notifications to bypassed users | Fixed |
Secret Double Octopus Authentication Server OS Support
Here’s the official OS support matrix. While Alma Linux isn’t listed, we’ve confirmed it works seamlessly with SDO.
| Linux base OS (64-bit) | Supported Versions |
|---|---|
| Red Hat | 8.2-8.10 Minimal image option |
| *Note Version 9.5 is a new addition to the supported OS | 9.3-9.5 Minimal image option |
| Oracle Linux | 8.3-8.10 |
| *Note Version 9.5 is a new addition to the supported OS | 9.3-9.5 |
| Rocky Linux | 8.4-8.10 |
| *Note Version 9.5 is a new addition to the supported OS | 9.3-9.5 |
Looking to integrate passwordless authentication into your organization?
Modernizing legacy apps or strengthening security? SDO 6.6.2 has you covered. Let’s discuss how passwordless MFA can transform your organization’s authentication strategy.
📩 Contact us to explore tailored passwordless authentication solutions! Learn more here.