
Zero Trust
Endpoint Protection
Endpoint Protection
Unparalleled Zero Trust Endpoint Protection for Every Business
Secure, Control, and Monitor Your Digital Environment with Precision
Direct Business Technologies is proud to partner with ThreatLocker® to offer a comprehensive suite of tools that provide more than just protection— they empower your organization to operate safely and efficiently in an increasingly complex digital world.
Tailored Solutions for Diverse Industries
ThreatLocker is engineered to adapt to various industry needs, providing targeted solutions that address specific challenges faced by businesses across sectors. From healthcare and finance to education and government, our platform ensures that your unique requirements are met with precision and scalability.
Core Features
Application Control – Total Governance Over Applications
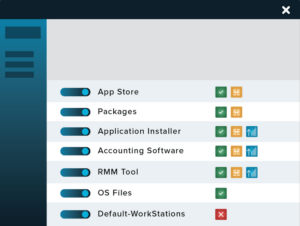 Allowlisting: Total Endpoint Control
Allowlisting: Total Endpoint Control
The first line of defense in cybersecurity should always be controlling what software can operate within your environment. Allowlisting is the backbone of ThreatLocker’s defensive strategy, allowing only approved software to run on your network. This approach blocks unauthorized applications automatically, significantly reducing the attack surface and enhancing your security posture.
- Robust Malware Defense: By only allowing pre-approved applications, you effectively block malware, ransomware, and other unauthorized software.
- Dynamic Policy Engine: Implement time-based and context-aware firewall-like policies to adapt to evolving security needs without manual intervention.
- Automatic Updates: Keep your system secure with minimal disruption by automatically updating application policies when new versions or patches are released.
Ringfencing™: Precise Application Behavior Management
Restrict how approved applications interact with your system, preventing them from executing harmful processes or accessing sensitive data.
Ringfencing not only prevents applications from executing unwanted processes but also restricts how they can interact with other applications, the system’s network, files, and registry settings. This capability is vital in combating fileless malware and other software exploits by ensuring that applications can only perform their intended functions without stepping outside their operational boundaries.
- Prevent Malicious Behavior: Limit the interaction of applications with critical system resources and other applications, reducing the risk of exploits.
- Protect Sensitive Data: Ensure that applications cannot access or modify sensitive files or settings unless explicitly permitted.
- Containment and Compliance: Enforce policy-driven boundaries around applications, which is crucial for compliance with data protection regulations.
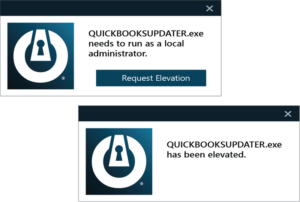 Elevation Control: Secure Administrative Privileges
Elevation Control: Secure Administrative Privileges
Grant necessary administrative privileges to applications without exposing overall system integrity, ensuring users operate within a secured boundary.
Elevation Control addresses the security risks associated with administrative privileges. By allowing specific applications to run with elevated rights under controlled conditions, ThreatLocker ensures that necessary tasks can be performed without compromising the overall security of your system.
- Granular Access Control: Determine which applications can run with elevated privileges and under what conditions.
- Integration with Ringfencing: Pair with Ringfencing to ensure elevated applications cannot misuse their privileges to affect other processes or systems.
- Streamlined Permissions: Simplify the management of administrative rights, allowing for quick response to legitimate user requests while maintaining strict security controls.
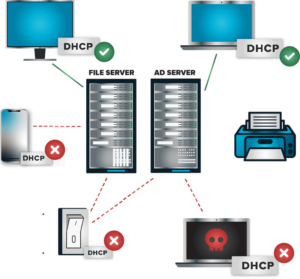 Network Security – Advanced Protection for Your Network
Network Security – Advanced Protection for Your Network
Network Control: Manage and monitor all network connections dynamically. Set granular access controls that adjust in real-time based on user activity and threat intelligence.
Dynamic ACLs: Automatically adjust network access based on user roles, behavior, and security posture, ensuring that only legitimate traffic is allowed.
Port Management: Control which ports are open on your Windows based systems, reducing potential entry points for cyber threats.
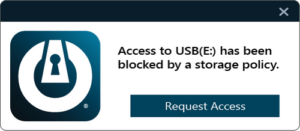 Data & Storage Security – Comprehensive Data Protection Strategies
Data & Storage Security – Comprehensive Data Protection Strategies
Storage Control: Regulate who can access data and how it’s accessed, preventing data breaches and ensuring compliance with data protection regulations.
Audit Trails: Maintain detailed logs of data access and transfers to manage compliance and audit requirements effectively.
USB and Device Control: Manage and monitor the use of removable storage devices to prevent data leakage and block malicious devices.
 Operational Efficiency – Enhance Your Cybersecurity without Compromising
Operational Efficiency – Enhance Your Cybersecurity without Compromising
Testing Environment: Deploy new applications in a controlled environment to assess potential risks before going live.
Automated Policy Updates: Ensure that security policies are automatically updated in response to new threats without requiring manual intervention.
Seamless Integration: Integrate seamlessly with existing IT environments to enhance security measures without disrupting existing workflows.
Around-the-Clock Support from Cybersecurity Experts
Our commitment to your security is around-the-clock. Our support team, based entirely in the US, is available 24/7/365 to assist with any concerns. With rapid response times, most issues are resolved within minutes of your call, ensuring that your operations continue smoothly without disruption.
Experience the peace of mind that comes with unparalleled security and control. Contact us today to learn more about our tailored solutions or to schedule a demo and see first-hand how we can help secure your operations against the ever-evolving landscape of cyber threats.